Archive for April 2016
How to Become an Ethical Hacker
Cyber-security is
one of the major concerns of online users these days and hackers are an
inevitable part of this discussion. Every part of our cyber world is influenced
by hackers and they exploit the vulnerabilities of systems to gain unauthorized
access. While numerous people are confused between the terms hackers and
cyber-criminals, many of you are willing to know more about hackers and how to
become one.
Have you ever considered hacking as a career?
There are few things that should be considered to figure out if hacking is the
right job for you.
As I’ve discussed in my earlier article, there is great confusion among people when it comes to things
like cyber criminals, hackers, ethical hacking, black hat hacking, white hat
hacking and more.
Who is an ethical
hacker?
Ethical hacker performs hacking to help an individual or company
and identifies the potential risks. An ethical hacker is a good guy and
sometimes the term is used synonymously White Hats. They work to improve the
overall internet security and search for weak points that could be exploited by
the black hats – the bad guys.
Take a look at these points and you will understand what
constitutes ethical hacking! These are “guidelines” that an ethical hacker must
follow!
1.
Respect an individual’s
or company’s privacy.
2.
Having a permission
(expressed – often written) to break into a network and look for the loopholes.
3.
After finding the
vulnerabilities, you tell your employer about the unknown flaws.
4.
After finishing the
work, you must not anything open for later exploitation by you or someone else.
5.
Do not take any kind of
advantage of the permission and access granted to you.
Now, take a look , It’s a very well
represented career path. For choosing this career as an ethical hacker, you can
start by becoming an Information Security analyst or by becoming a computer
programmer.
Learn more about this
career path in the info-graphic given below:
To Build a best Career as Security Professional :
Contact :
Redback IT Academy
#AL 24, TNHB , PHASE III,
Sathuvacheri,
Near Vallalar Water Tank ,
Vellore.
Call us @ : 8189985551
Tuesday, April 26, 2016
Posted by Sivapriya
The 7 Most Wanted Iranian Hackers By the FBI
The Federal Bureau of Investigation (FBI) has lengthened its Most Wanted List by adding seven Iranian hackers who are
accused of attacking a range of US banks and a New York dam.
The United States Department of Justice (DoJ) charged seven Iranian hackers with a slew of computer
hacking offences for breaking into computer systems of dozens of US banks,
causing Millions of dollars in damages, and tried to shut down a New York dam.
The individual hackers, who allegedly worked for computer
security companies linked to the Iranian government, were indicted for an
"extensive campaign" of cyber-attacks against the
US financial sector.
All the seven hackers have been added to the FBI's Most Wanted list, and their names are:
1.
Ahmad Fathi, 37
2.
Hamid Firoozi, 34
3.
Amin Shokohi, 25
4.
Sadegh Ahmadzadegan (aka Nitr0jen26), 23
5.
Omid Ghaffarinia (aka PLuS), 25
6.
Sina Keissar, 25
7.
Nader Saedi (aka Turk Server), 26
All the hackers have been charged with conducting numerous
Distributed Denial-of-Service (DDoS) attacks on major U.S. banks, with Firoozi
separately gaining unauthorized access to a New York dam's industrial
automation control (SCADA) system in August and September of 2013.
"This
unauthorized access allowed [Firoozi] to repeatedly obtain information
regarding the status and operation of the dam, including information about the
water levels, temperature, and status of the sluice gate, which is responsible
for controlling water levels and flow rates," a DoJ statement reads.
Luckily, the sluice gate had already been manually
disconnected for the purpose of maintenance at the time Firoozi attacked.
The hackers' work allegedly involved Botnets – networks of compromised machines – that
hit major American banks, including Bank of America and J.P. Morgan Chase, as
well as the Nasdaq stock exchange with floods of traffics measuring up to 140Gbps and knocked them offline.
The Iranian hackers targeted more than 46 financial
institutions and financial sector companies, costing them "tens of Millions of dollars in remediation costs"
in preventing the attacks in various incidents spanning 2011 to 2013.
All
the seven hackers will face up to 10 years in prison on computer hacking
charges while Firoozi faces an additional 5-year prison sentence for breaking
into a dam in Bowman Avenue Dam in Rye Brook, New York.
WhatsApp’s end-to-end encryption: How to enable and what it means.
WhatsApp is now end-to-end encrypted at all times. This will ensure that a user’s messages, videos, photos sent over WhatsApp, can’t be read by anyone else; not WhatsApp, not cyber-criminals, not law-enforcement agencies. Even calls and group chats will be encrypted.
WhatsApp co-founder Jan Koum announced the update on his Facebook page, stating that the company has been working on the feature for the last two years.
Koum wrote, “We’ve been working for the past two years to give people better security over their conversations on WhatsApp… People deserve security. It makes it possible for us to connect with our loved ones. It gives us the confidence to speak our minds. It allows us to communicate sensitive information with colleagues, friends, and others. We’re glad to do our part in keeping people’s information out of the hands of hackers and cyber-criminals.”
So what is end-to-end encryption and how exactly does it work in WhatsApp?
WhatsApp is using “The Signal Protocol”, designed by Open Whisper Systems, for its encryption.
In its White Paper, explaining the technical details of the end-to-end encryption, WhatsApp says that “once the session is established, clients do not need to rebuild a new session with each other until the existing session state is lost through an external event such as an app reinstall or device change.”
The post explains how messages are encrypted as well. It reads, “clients exchange messages that are protected with a Message Key using AES256 in CBC mode for encryption and HMAC-SHA256 for authentication. The Message Key changes for each message transmitted, and is ephemeral, such that the Message Key used to encrypt a message cannot be reconstructed from the session.” It also says that calls, large file attachments are end-to-end encrypted as well.
Note the ever-changing message key can mean a delay in some messages getting delivered, according to the paper. It should be noted that feature is enabled by default in WhatsApp, which means that if you and your friends are on the latest version of the app, all chats will be end-to-end encrypted. Unlike say Telegram where users have to start a secret chat to enable the feature, WhatsApp has the feature on at all times. Users don’t have the option of switching off end-to-end encryption.
Users need to be on the same versions of WhatsApp to ensure that their chats get end-to-end encrypted. If you’ve recently updated the app, and you start a chat with someone else (also on the new version) you are likely to see a message saying, “Messages you send to this chat and calls are now secured with end-to-end encryption.
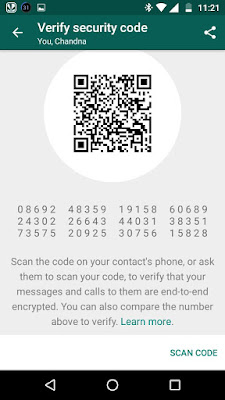
Once you tap on the message, WhatsApp has a pop-up menu explaining what end-to-end encryption means. Users can verify if the encryption is working as well. If a user taps on verify, they will taken to a page with a QR code, followed by a string of 60 numbers. If your friend is nearby, take their phone scan the code from your phone (the option is there at the bottom of the same page) and if the QR code matches, then the chat is encrypted. When the codes match, a green tick appears; when it doesn’t there’s an exclamation mark in red alerting a user that the chat is not secure. So does the end-to-end encryption work all the time? We tried verifying some chats that had the message saying encryption was enabled. In some cases, the verification failed for us. In the first case, we tried to verify a chat between an Android and iPhone 6s device (running iOS 9.3.1), and the QR codes didn’t match. We also tried matching QR codes on an two Android phones, and once again we got the red alert indicating no end-to-end encryption
.
Android phones are on the latest version of the app from the Google Play Store. However a verification between a chat on two iOS devices, (iPhone 6s, iPhone 5s) worked for us and showed the green tick. We’re not sure why the verification failed, even though the chat says it is end-to-end encrypted. We might have to wait for another app update that could fix this issue.